2 min read
Important Security Update on OpenPrinting CUPS Vulnerabilities
Several vulnerabilities were recently discovered in CUPS (Common UNIX Printing System), a widely used open source printing system. These vulnerabilities, which could potentially impact your system, should be remediated immediately. Follow our instructions below to determine whether your system is vulnerable and how to protect it immediately.
Overview of CVEs:
The following vulnerabilities have been identified in CUPS:
- CVE-2024-47076
- CVE-2024-47175
- CVE-2024-47176
- CVE-2024-47177
This combination of vulnerabilities could allow an attacker to potentially perform remote code execution.
Who/What Is Affected:
Only systems running the service (which is not default) are affected. If your system is running that service, we recommend applying the following immediate workaround until a permanent fix is available:
These vulnerabilities impact all versions of CUPS prior to the latest update. Systems running UNIX-based distributions that have CUPS enabled are potentially exposed.
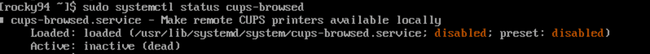
To check if your system has CUPS enabled, you can run the following command:
sudo systemctl status cups-browsed
- If the result includes “Active: inactive (dead)” then your system is not vulnerable to this attack
- If the result is “running” or “enabled,” and the CUPS-browsed configuration file at /etc/cups/cups-browsed.conf “BrowseRemoteProtocols” directive contains the value “cups”, then the system is vulnerable.
- By default, the CUPS daemon listens only on localhost which would require an attacker to already have local access to the machine. If the CUPS configuration file at /etc/cups/cupsd.conf contains only a “Listen localhost:631”, the attack cannot be trivially performed remotely.
Immediate Steps to Protect Your System:
We recommend applying the following immediate workaround until a permanent fix is available:
To stop the service, an administrator can run the following command:
sudo systemctl stop cups-browsed
Disable remote printing access if it's not required in your environment. To prevent the cups-browsed service from starting on reboot, run the following command:
$ sudo systemctl disable cups-browsed
Monitor print jobs and logs for any unusual activity or unexpected access requests to the printing system.
You can also watch our quick video demonstration on how to fix the CUPS CVE vulnerabilities:
Long-Term Remediation:
CIQ is actively working on patches to address these vulnerabilities. We highly recommend monitoring your system for updates and applying the patch as soon as it's released.
We will continue to keep you updated with any new developments and will provide guidance once the official patches become available. In the meantime, please reach out to us at support@ciq.com if you have any questions or need further assistance.
Built for Scale. Chosen by the World’s Best.
1.4M+
Rocky Linux instances
Being used world wide
90%
Of fortune 100 companies
Use CIQ supported technologies
250k
Avg. monthly downloads
Rocky Linux