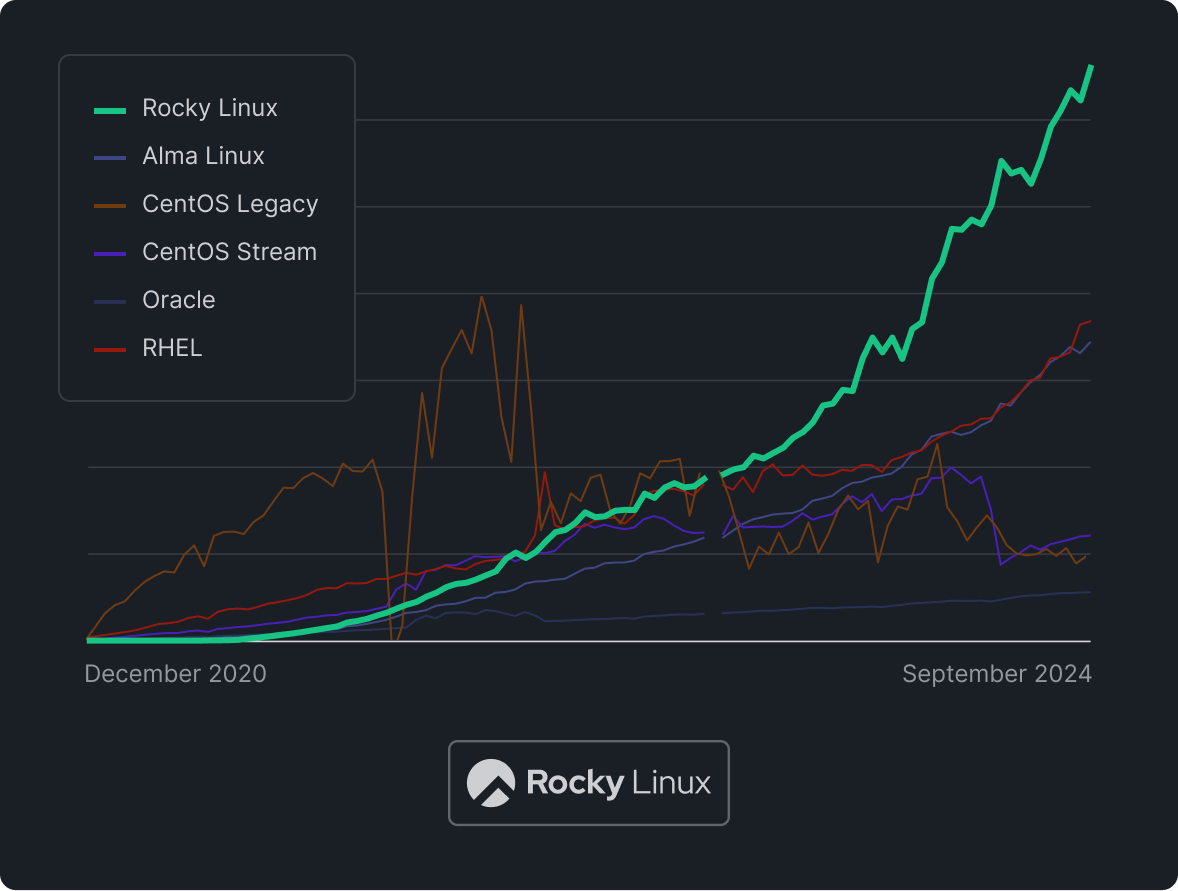
Enterprise Linux, adopted by millions
Open source Rocky Linux ...
Since its inception over four years ago, Rocky Linux has become the trusted open -source option for businesses seeking a rock-solid, Enterprise Linux distribution.
CIQ is the founding services and support sponsor of the project and with Rocky Linux from CIQ; we augment the open source distribution with secure delivery, reliability, and support so that you have the assurances you need for production workloads.
… optimized for your use case by CIQ.
Rocky Linux from CIQ delivers enterprise guarantees and also offers optimizations for the discrete requirements of your environments. You can also use open source Rocky Linux with each of these and ensure consistency and compatibility.
Rocky Linux from CIQ (RLC)
Enterprise Linux, binary compatible with open source Rocky Linux with support, indemnification, service level objectives, and package validation.
RLC - Hardened
Built on RLC, Rocly Linux from CIQ- Hardened adds optimizations for security hardening. Built for environments with increased security requirements.
RLC: Enterprise Linux with guaranteed updates, delivered securely.
All versions of Rocky Linux from CIQ deliver validated and secure images with a commercial SLOs for updates
Security updates
guaranteed with SLO
RLC delivers validated security updates (when necessary) with a commercially backed SLO (within ~30 days of release) to ensure that even if the upstream community is delayed or if they decide not to fix a critical security issue, CIQ will ensure you are compliant and up to date.
Verified and validated
for secure delivery
With RLC, CIQ validates all installers, community packages, binaries, metadata, and errata, and all delivery is sourced from dedicated CIQ repositories in US-based datacenters that are mirrored across time zones and cloud regions.
RLC: Right image, right environment,
right cost.
Consistent environments, one price, no tracking audits
Rocky Linux from CIQ offers a simple, low-cost site license, and we’ll only track how much data has been downloaded, so you are free to use RLC on as many nodes as you like without audit. You can use a consistent enterprise Linux distribution in ALL your environments and know that we’ve got your back in production.
Consistent environments
Use the right image in dev and test and then get guarantees in prod with Rocky Linux from CIQ.
Without the exorbitant cost
We simply charge a flat rate for access to RLC and then set an upper limit on gigabytes pulled so there is no audit by node or instance.
Rocky Linux and Rocky Linux from CIQ.
CIQ engineering is deeply involved in the open source Rocky Linux project. From development to delivery, we are committed to the long-term success of this important open source project. It’s in our DNA.
What are the differences?
Rocky Linux is trusted by thousands and reliably meets most enterprise requirements; however, there are a few items the community does not focus on and CIQ is here to ensure those requirements are met. The differences are outlined below:
RLC: Supported and indemnified.
World class 24x7 support with guarantees
CIQ support
CIQ offers personalized support, deep technical expertise, and enterprise-grade SLAs for Rocky Linux from CIQ. We offer standard break/fix support and premium levels for environments that require timely fixes through short SLAs.
Indemnification
Rocky Linux from CIQ comes with protection and indemnification guarantees that mitigate your risk and liability in the case of legal issues. CIQ is accountable and delivers the coverage to keep your legal and compliance teams satisfied.
Rocky Linux, CentOS, and CIQ.
CIQ Bridge allows you to migrate from CentOS to Rocky Linux from CIQ
With the discontinuation of CentOS over four years ago, many critical production applications lack a supported and current base OS.
Rocky Linux from CIQ is the industry choice to upgrade from CentOS so you can have long-term stability and a compatible distribution for your CentOS applications. With CIQ Bridge we make this transition as painless as possible.
Why Rocky Linux From CIQ?
CIQ delivers the right choice for adoption of Rocky Linux for organizations that require consistent environments, availability guarantees, heightened security, and compliance.